Managed Detection and Response
Secure your business against sophisticated cyber threats with our premier cybersecurity solutions. Our AI-driven managed detection and response (MDR) solutions offer a proactive defence strategy, combining 24/7 monitoring with extended threat detection and rapid incident response. Our team of cybersecurity experts utilises advanced technologies like AI-driven analytics, machine learning, and threat intelligence to identify and neutralise potential threats before they escalate. With real-time alerts and comprehensive threat investigation, we ensure that your systems remain secure from vulnerabilities and breaches. Additionally, our MDR services include continuous vulnerability assessments and customised response plans, tailored to fit your unique security needs. You gain peace of mind with a robust security framework that adapts to evolving threats and delivers immediate, effective protection by choosing our MDR solutions. Rely on our expertise to fortify your cybersecurity posture and maintain the integrity of your critical digital assets.
Remote Management and Monitoring
Remote Management and Monitoring
The Remote Management and Monitoring (RMM) Tool is a cloud-based central platform that allows IT experts to manage digital infrastructure. The key features that transform IT and OT management include real-time monitoring, remote access and control, recoding of remote sessions for audit purposes, bulk deployment of policies and applications, automated operation systems and application updates, threat and vulnerability management, application control, comprehensive reporting and analytics. Our RMM solution allows us to remotely troubleshoot IT issues, resulting in a quicker resolution. Additionally, our RMM solution provides instant alerts and notifications based on anomalies, allowing us to address the problems before they escalate, ensuring the smooth operation of your digital environment. You can use the RMM tool as a substitute for Microsoft Intune in managing mobile devices, which includes controlling operating systems and applications on kiosks.
Vulnerability and Patch Management
One of the key aspects of cybersecurity and maintaining cyber hygiene is to keep the IT and OT infrastructure up-to-date. We exclusively feature automated vulnerability and patch management as a complement to the remote monitoring and management tool. Alternatively, we also offer solutions that conduct thorough scans to detect potential weaknesses or vulnerabilities in the operating system, network, firewall, and OT systems. We prioritise critical patches based on risk assessment and deploy updates with minimal disruption to your operations, applying timely and effective patches to protect against emerging threats and vulnerabilities. Our proactive management ensures that your software and operating systems are up-to-date, reducing the risk of cyberattacks and enhancing overall system performance. By implementing our vulnerability and patch management solutions, you safeguard your network from potential breaches and ensure compliance with industry standards, maintaining a secure and resilient IT environment. Trust us to keep your systems fortified and running smoothly, adapting to new threats with precision and efficiency.
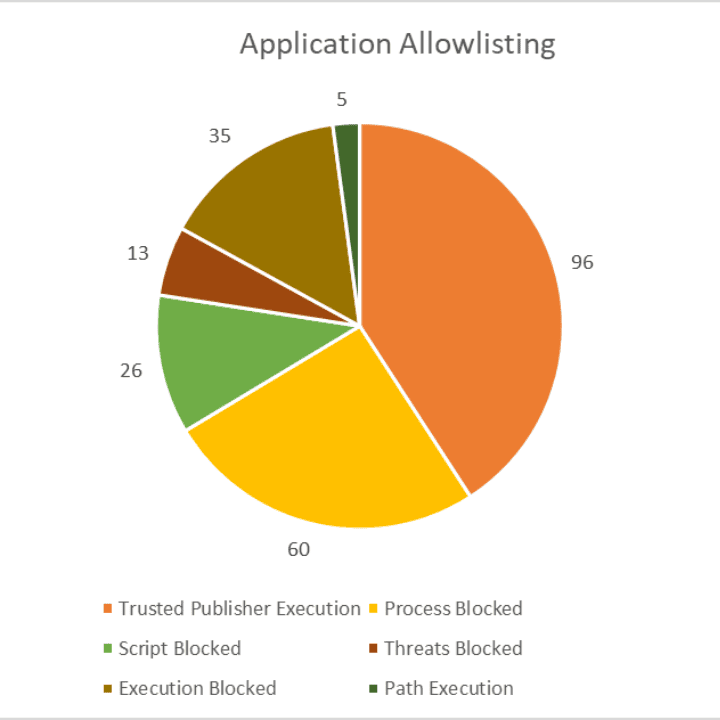
Application Control
Application Control
Does your organization permit applications, processes, and scripts to run on computer systems? By leveraging features such as blocking malware, ransomware, scripts or processes, and unsigned or unsanctioned applications, we offer a premium managed solution to control the installation of applications on endpoints. For a seamless experience, end users can request approval directly from the agent if the application meets organization policy. With our expert support, you gain enhanced control over your software environment, maintain compliance with security policies, and protect your critical data from malicious attacks. Use our allow-listing SaaS application to strengthen your security posture, streamline software management, and ensure a safer, more reliable IT or OT infrastructure.
Anti-virus and Drive Encryption
As reliance on technology grows, so does exposure to cyber threats. Over time, we have seen an increase in cyber attacks such as USB viruses, phishing, ransomware, spyware, botnets, adware, and data breaches that have led to unauthorised access, resulting in identity theft and privacy violations, data erasure, disruptions to business operations, and financial and reputational damage. We offer premium anti-virus solutions that not only provide a centralized cloud platform to manage devices and policies, but extend to other cloud apps and networks for compressive protection and analytics. We have partnered with cybersecurity industry experts, enabling us to plan and implement the best solutions to protect your digital environment.
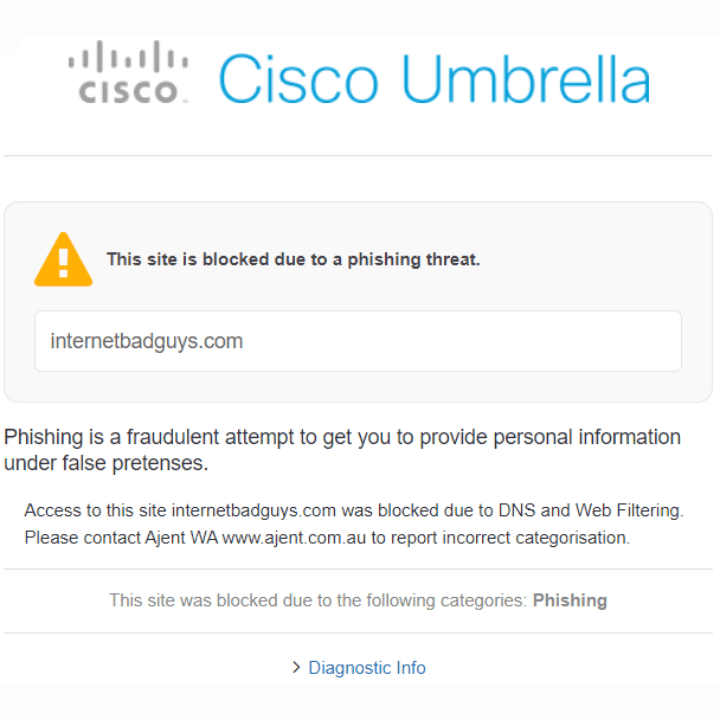
Web Content Filter and DNS Protection
Web Content Filter and DNS Protection
In a time when the internet has become essential to daily life, over 80% of online threats arise from browsing and surfing the web. We offer an exceptional web content filtering service that shields your online activities from monitoring or tracking through advertisements, links, and cookies, and prevents you from falling victim to malicious and phishing sites. By employing advanced filtering technologies, you can block harmful websites and content that present security risks. This helps prevent users from unintentionally accessing dangerous sites that could result in data breaches, phishing incidents, or exposure to unsuitable material. The integration of Secure Access Service Edge (SASE) technology enhances your online security by merging various cybersecurity solutions into a single framework. SASE offers seamless, cloud-based security services, encompassing content filtering, DNS protection, SSL inspection, phishing safeguards, data loss prevention, and malware defence. This comprehensive method guarantees extensive protection and enhances security effectiveness. Contact us today to learn more about our tailored solutions and how we can help you achieve robust, reliable protection for your digital environment.
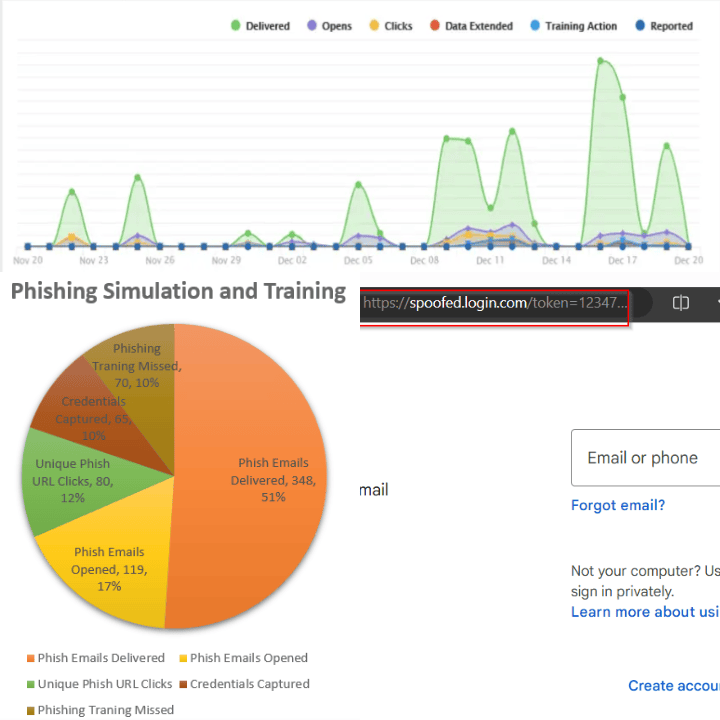
Phishing Simulation
Empower your workforce with our all-encompassing email phishing simulation and training programme solutions. Stay one step ahead of potential threats through our monthly email phishing simulations. We design these simulated attacks to mimic real-world scenarios, enabling you to assess your organisation's vulnerability to phishing schemes. Regular simulations offer valuable insights into your team’s ability to identify and react to phishing attempts, facilitating ongoing enhancements to your defences. The training platform aims to instruct your team on recognising and responding to phishing efforts, thereby boosting their capability to discern fraudulent emails and avoid common traps. Additionally, the short, engaging, and interactive training sessions guarantee that your staff is adequately equipped to manage phishing threats effectively. Our solution features comprehensive reporting and analytics to monitor the success of your phishing simulations and training initiatives. Obtain actionable insights regarding your organisation's vulnerability to phishing, recognise patterns, and assess progress over time. Our reports deliver a clear overview of your security standing, empowering you to make informed choices to bolster your defences. Furthermore, you can seamlessly integrate our email phishing solutions with your current learning management system (LMS). This integration simplifies the management of your cybersecurity training programmes and offers a centralised platform for tracking progress and ensuring compliance.
Domain and DNS Management
Domain and DNS Management
Registering domain names and managing DNS entries might seem overwhelming, yet they are the first crucial step in protecting your brand name. We take care of the complex nuances of DNS and domain name maintenance. DNS records like NS, SOA, A, MX, CNAME, and TXT necessitate meticulous attention. Every record has a specific purpose. For example, CNAME and TXT records point to various services or apps, MX points to mail servers, and A or AAAA records point to the website address. We are here because we understand the complexity involved. You not only get the best prices through our partnerships with distributors, but you also benefit from our annual maintenance services, which ensure your online operations are agile and resilient.
Email Security
Emails form a critical role in conducting day-to-day business operations, and securing email in the inbox or in transit becomes non-negotiable. Our expert email security solutions, tailored to thwart phishing attacks and protect your communications, can enhance your organisation's cybersecurity. Our sophisticated email security solution leverages AI-powered threat analytics for real-time detection and prevention of phishing attempts. Whether implemented as an MX record or an Azure enterprise application, our solution integrates effortlessly into your existing framework. The product quickly identifies and eliminates malicious or phishing emails, ensuring that your inbox is secure and your organization is well protected. Contact us to know more about our comprehensive email security offerings to combat emerging threats and preserve the integrity of your digital communications.